When Does a Smart Contract Audit Actually Expire?

An audit does not fail overnight. It expires quietly. Most Web3 teams treat “Was Audited” as a durable security signal. But a smart contract audit validates a specific version of code, under a specific set of assumptions. And those assumptions rarely stay static. So the real question isn’t whether audits are important. It’s this: When […]
Fidesium January 2026 Product Update: Preserving Audit Value as Code Ships Faster

Why do smart contract audits lose relevance so quickly? Because every meaningful code change introduces uncertainty that the original audit never reviewed. December’s updates focus on one core goal: making audits last as protocols evolve, tooling scales, and teams ship faster. This month, we strengthened audit continuity across three critical areas: Interoperability with existing security […]
Why Smart Contract Security Tools Struggle With Noise

– and How Fidesium Changes the Game False positives are one of the biggest blockers to effective smart contract security. They waste developer time, slow audits, and quietly erode trust in automated tools. The problem is not static analysis itself, it’s the lack of contextual understanding around findings. In this blog, we break down: why […]
Fidesium December 2025 Product Update: Smarter Detection, Continuous Protection, Real-World Coverage

Web3 is moving fast, and so are the threats. This month, we’ve shipped some of our biggest improvements yet, focusing on continuous protection, higher detection accuracy, and smarter analysis of real-world smart contract behaviour. Below is everything that’s new across the Fidesium platform and detection engine. Platform Improvements These are the platform improvements that […]
Audits Age. Attackers Don’t. Why Continuous Security Is Now Mandatory in Web3

For years, Web3 teams have treated security audits like a milestone: something you complete once, check off, and move past. But as the ecosystem grows – and as attackers become more sophisticated – one truth has become impossible to ignore: An audit is a snapshot.Attackers operate in real time. The exploit of a Yearn smart […]
SafeDrop Linea Airdrop Audit Validation: Evidence, Integrity, and Why It Matters for Web3 Security

Fidesium verified SafeDrop’s Linea airdrop case study, confirming coordinated wallet activity and the technical soundness of its codebase. Here’s what the findings reveal about Web3 transparency, and why continuous, evidence-based auditing is becoming the new security standard. What Is the SafeDrop Linea Airdrop Audit Validation? In short, it’s an independent technical verification conducted by Fidesium […]
Chadi Sebbar’s Journey into Smart Contract Security

Web3 security isn’t just about code, it’s about the people who dedicate their careers to protecting the ecosystem, and with it a vision for a better future. One of them is Chadi Sebbar, a multilingual security engineer whose unique path shows what it takes to build trust in a decentralized world. Who This Story Is […]
Formal Analysis in Web3: What Founders Need to Know (Without the Math)

If you’re a Web3 founder, you’ve probably heard terms like testing, fuzzing, audits — and now formal analysis. At first glance, they can sound like the same thing.They’re not. Here’s the simplest way to think about it: Fuzzing tries to find failures.Formal analysis proves failures cannot exist. Fuzzing is powerful. It throws thousands of random […]
NPM Supply Chain Attack: Wallet Address Swap Trick

In this article, you’ll learn: How attackers used a string-similarity algorithm to trick users with look-alike wallet addresses. Why even experienced developers can be misled by UI-level deception. What this attack reveals about supply chain risks in Web3. Practical steps to protect your code, transactions, and community trust. At Fidesium, we keep a close eye […]
Fidesium PB&J Case Study
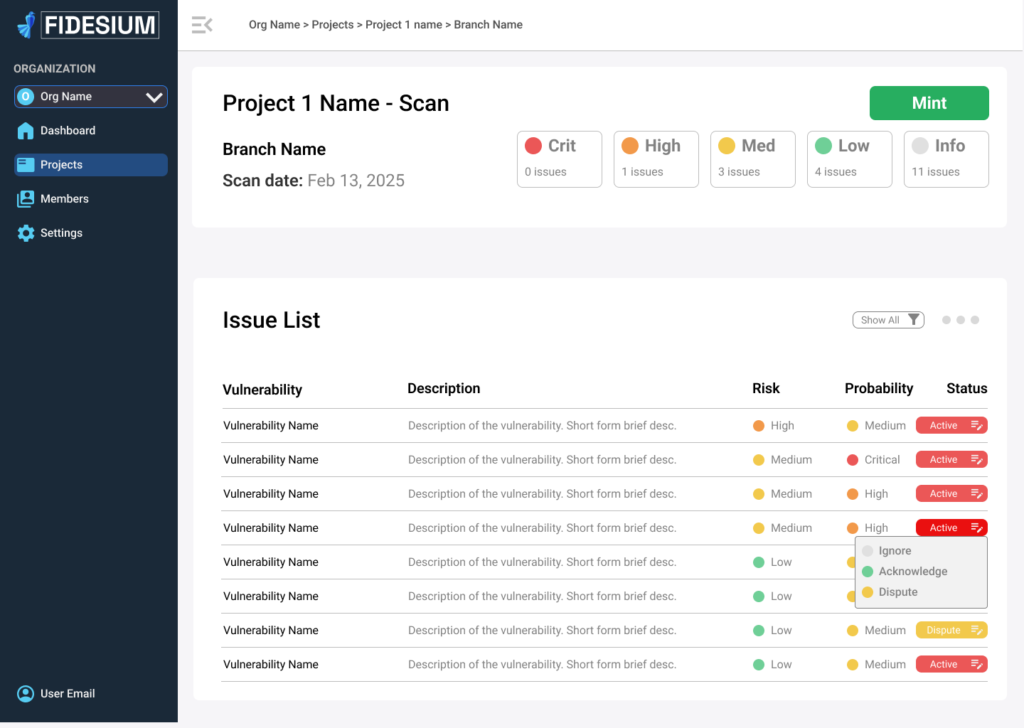
Security as a process allows companies to launch quickly and on schedule. In the world of blockchain and Web3 development, security is not merely a checkpoint but a continuous process. When done correctly it empowers organizations to innovate boldly while mitigating risks. This approach transforms potential vulnerabilities into opportunities for refinement, allowing PB&J to launch […]