This write up will look at a flavour of social engineering scam that’s been emerging in the current VC winter.
Earlier this week we got connected on Telegram to somebody who claimed to work for https://fenbushi.vc/, a pioneering Asian crypto VC. After some initial discussion in Telegram, we agreed to schedule a call to take them through our business. So far, so good, standard fundraising fare.
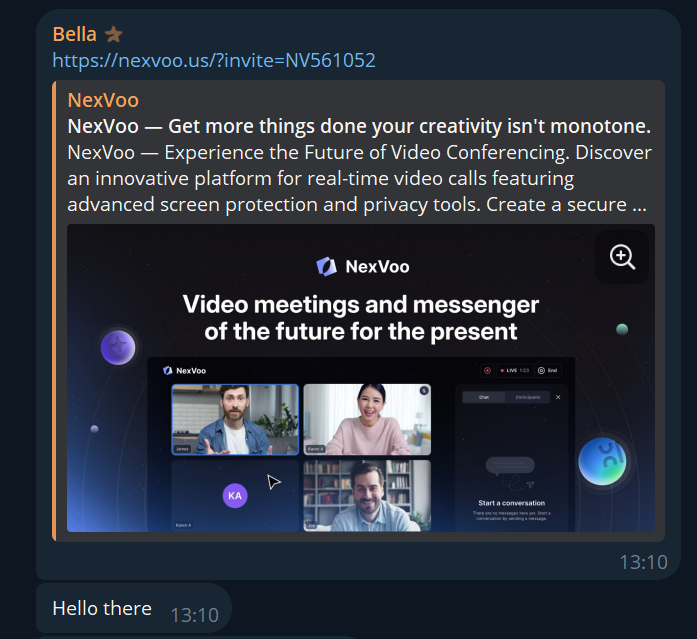
The person in question worked for a subsidiary of Fenbushi in investor relations (or at least that’s what her TG handle suggested). LinkedIn seemed valid. The first orange flag – why is someone in Investor Relations talking to a start-up? A Calendly link was shared, and a meeting scheduled.
This is where the first red flags began to appear. To keep readers secure and avoid clicking malicious links, even by accident, I am not going to be providing full URLs. Suffice it to say that the link provided for video conferencing pointed at nexvoo with a weird top level domain. What’s a nexvoo you may ask? A video conference camera manufacturer. Still just about believable enough, but their website is nexvoo.com, and their documentation suggests integrations with Google meet. Nothing whatsoever about their own conference software. Smelling fishier and fishier.
So, as any good security company would, we started digging. Turns out the domain name in question was registered a month ago. To a clearly fake email address, in Surat Alabama, at a non-existent Zipcode, and a phone number with the wrong number of digits. Searching for the business name, comes up with a handful of equally suspicious looking domain registrations, none of them older than 4 months (see screenshot 1).
Checking the MX records shows mail servers hosted at mx1.hosting.reg.ru. Now, reg.ru is a major Russian hosting provider. There are plenty of websites hosted there which are not in and of themselves malicious. But why on earth would a company from Alabama, host in Russia? And given the prevalence of cybercrime coming out of Russia, we decided to dig even deeper.
Turns out there were more red flags. The SSL certificate was fresh, and has an expiration date in the near future.
Firing up a malware scan against the URL we quickly found:
- The Domain spawns subprocesses, probing the system for information. (Are you on a Mac? Windows? Do you have Metamask installed? Etc)
- Highly suspicious network patterns, accessing a PHP server, and downloading a binary file (It should be self evident why this is bad – a common pattern will be wallet drainers)
- The domain signs messages with multiple (14) mixed certificate authorities. (This is a common evasion technique. It suggests stolen or leaked certificates, and attempting to trick whitelisting software).
There was also a variety of other smells, but these three were in and of themselves enough. Suffice it to say, we did not take this call.
So what is the learning here? What happens next?
As members of the security community we have filed reports with Cloudflare and Reg.RU to have the website shuttered. This is ultimately a fruitless exercise in whackamole, but if we can make the Russian hacker’s life a touch harder, all the better.
As active members of the crypto space, we advise you to always be vigilant. Never click non standard video call links. Always consider the source of every connection and how much you trust them. If something smells off, you’re better off not engaging.
Unfortunately, there isn’t a whole lot Fenbushi can do here. Putting a disclaimer on their website *may* be a Good Samaritan act.
NexVoo could consider buying up alternative domains.
Ultimately this is a question of good, individual OpSec, and healthy company policy. We here at Fidesium, happily help our customers establish secure policies, and train employees to identify and avoid such scams. Talk to us if this is a service you need.
Stay safe out there!