Competition-proven auditors backed by advanced automation,
kept relevant by continuous automated protection
Enterprise level security at a fraction of traditional costs
$250M+ Secured
110+ Contracts Audited
67% Lower Cost
Audis Last 40% Longer
Including teams operating audited contracts in production.
Version-linked. Publicly verifiable. No marketing edits.
Our clients love the speed, accuracy and cost of Fidesium automated audits.





You shouldn’t have to choose between security and speed-to-market.
Security should not hinder your growth, drain your pocket and slow your project.
The best of both worlds: thorough human review with 24/7 automated monitoring
Bundle & Save: Get manual audit + 6 months continuous monitoring at 30% off
Advanced static analysis and AST analytics scans your contracts
→ Surface critical issues in minutes, not weeks
Auditors use static analysis insights to help go deeper
→ Find sophisticated vulnerabilities automation misses
Automated rescans verify every fix
→ Faster turnaround, lower revision costs
Static analysis runs on every PR automatically
→ Prevent vulnerabilities from entering production
Detection improves as threat landscape changes
→ Your security gets smarter over time

Scans run during development
Issues discovered before manual review
Fidesium continuous coverage
Automated audit scans
GitHub integration
Nightly vulnerability reports
Community support
Price: $399/month or $3499/year
Full manual audit
1 month continuous scanning included (EVM)
Fix verification
Public audit report + badge +NFT
Priority support
Price: Starting at $5,000
Comprehensive manual audit
12 months continuous coverage
Quarterly re-audits
Security consulting (10 hours)
Dedicated auditor access
SLA + priority incident response
Price: Custom
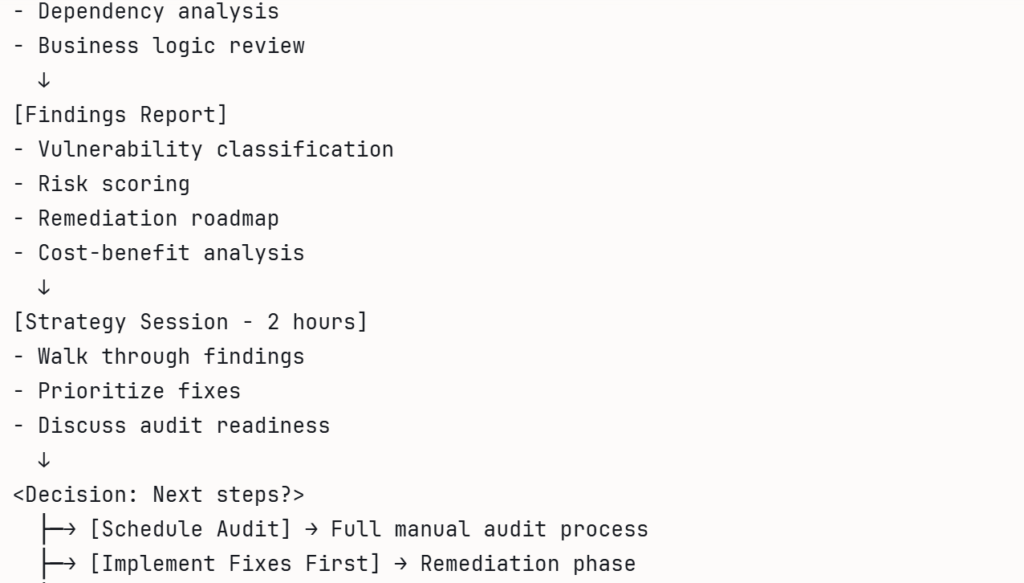
Traditional audits review your code at a single point in time.
Once code changes, the assumptions behind that audit may no longer hold.
Fidesium extends the value of audits over time.
It supports both manual and automated audits by re-running audit-grade checks when meaningful code changes occur, helping teams understand what remains covered, what needs review, and why.
This turns audits from static reports into version-aware security evidence.
The difference? We offer the same quality of security at 60-70% lower cost because our business model includes an ever improving tool to help our auditors and ongoing automated coverage that reduces the need for expensive re-audits. We also offer a machine readable verifiable record of your audit history as an NFT
Yes.
Automated tools catch ~89% of common vulnerabilities, but complex business logic, novel attack vectors, and context-specific issues require human expertise. Our hybrid model gives you both.
If our continuous scanning detects a new vulnerability post-deployment, we alert you immediately with severity classification and remediation guidance. Critical issues get direct contact with an auditor.
Most audits complete in 1-3 weeks depending on complexity. We provide a detailed timeline during scoping.
Traditional manual audits often force teams into costly re-audits after even minor changes. Fidesium reduces this overhead by covering incremental updates through continuous automated rescanning, limiting manual re-reviews to meaningful architectural changes and cutting re-audit costs by up to 60%.
Solutions vary on a case to case basis, but in general;
Pre-launch architecture reviews, security roadmaps, post-incident response, compliance guidance, and ongoing advisory.
Available as standalone service or bundled with audits.
Fidesium’s scanner, relies on many open source frameworks and extends them significantly.
1000+ custom detectors for critical edge cases.
Fidesium’s scanner is also change-aware, and fits into your development flow. Making it easier and faster to scan code as it develops. SARIF generation for compliance and interoperability.
CI/CD integration, reduces friction, deployment gate to stop vulnerable code from hitting production.
Free trial, no credit card
Scan your first repo in 60 seconds
Upgrade to manual audit anytime
Upload your repo for instant quote
Turnaround: 1-3 weeks
Starting at $5,000
30-minute strategy call
Security roadmap recommendations
No pressure, no obligation
Fidesium is a security platform dedicated to making automated smart contract audits continuous, accessible, and affordable for Web3 teams worldwide.
Copyright @ Fidesium LTD 2023. All Rights Reserved.