In this article, you’ll learn:
- How attackers used a string-similarity algorithm to trick users with look-alike wallet addresses.
- Why even experienced developers can be misled by UI-level deception.
- What this attack reveals about supply chain risks in Web3.
- Practical steps to protect your code, transactions, and community trust.
At Fidesium, we keep a close eye on supply chain exploits like this
A Clever Attack
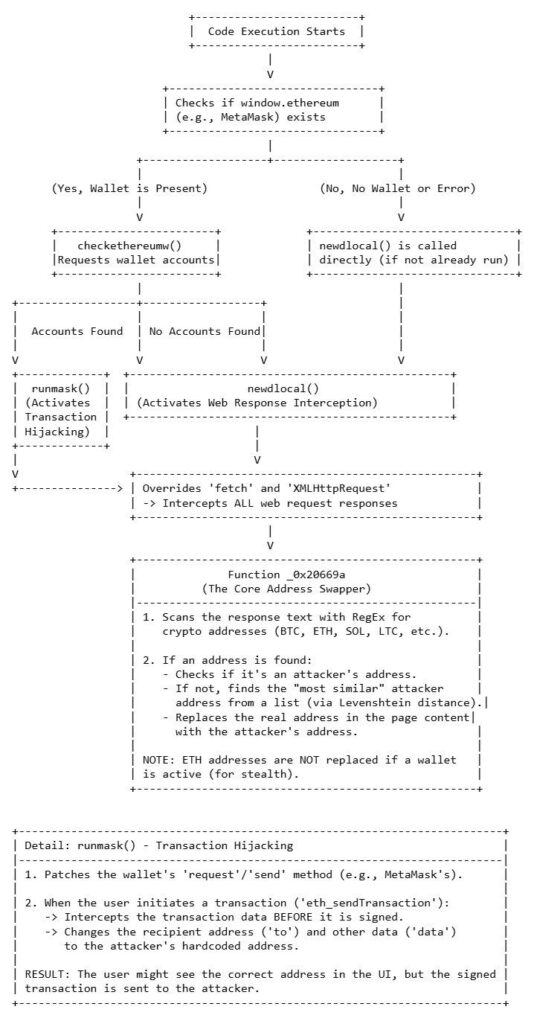
On Sept 8, 2025 we saw a really interesting NPM supply chain attack that shows just how inventive malicious actors can be in Web3.
The idea was simple, but executed creatively:
- Intercept web requests: the malware hooked into basic web APIs (fetch, XMLHttpRequest) so it could quietly intercept and alter outgoing traffic.
- Swap recipient addresses: it replaced wallet addresses with attacker-controlled ones.
- Look-alike trick: to make the swap less noticeable, it used the Levenshtein distance algorithm to pick an attacker address that looked nearly identical to the original.
- Wallet API hooks: when a wallet like MetaMask was present, the malware hooked into methods such as eth_sendTransaction, so that on-screen users still saw the “correct” address – but the signed transaction was silently redirected to the attacker.
Impact of the Attack
Ironically, after all this technical creativity, the attackers only managed to steal around $500 before detection.
From a cybersecurity perspective, though, this was significant work:
- Clever use of string similarity algorithms.
- Seamless integration into normal wallet flows.
- Exploiting human trust in visual confirmation.
And yet, the immediate defence remains straightforward:
Always double-check the receiving address before approving a transaction, ideally on a hardware wallet screen.
Lessons Learned for Web3
Even though the financial damage here was small, this attack illustrates several broader risks for blockchain developers and users:
- Supply chain vulnerabilities: a single compromised account can push malicious updates to packages buried deep in your dependency tree.
- UI deception: even if users think they are verifying details, API hooks can alter execution under the surface.
- Small attacks, big lessons: many large-scale exploits begin as low-value test runs to refine techniques.
The takeaway: Security has to extend beyond smart contracts.
Your entire toolchain – dependencies, build pipelines, and CI/CD – needs to be treated as a potential attack surface.
How to Stay Protected
- Harden your CI/CD: enforce immutable installs (npm ci, frozen lockfiles) and require 2FA for maintainer accounts – the initial compromise here came from phishing.
- Verify addresses manually: never rely solely on the address shown in your dApp’s UI.
- Audit your dependencies: treat supply chain risks with the same seriousness as contract audits.
- Pin safe versions: after this incident, projects should pin affected libraries to the last known-good versions to avoid silent pulls.
- Integrate continuous monitoring: automated scanning and alerts help catch unusual behavior early.
How Fidesium Approaches Security
At Fidesium, we study incidents like this because every trick offers valuable insights.
Our approach focuses on:
- Continuous, automated audits that evolve with your repository.
- Vulnerability detection for Web3 so that projects can launch with confidence.
- Building security as a process – not a one-time event.
Whether you’re a small team or a large protocol, our mission is to help you ship secure smart contracts and protect your community.
Final Thoughts
This attack may have been small in financial terms, but it reinforces how creative and persistent malicious actors are becoming in Web3.
The best defence isn’t panic – it’s a culture of continuous security, from dependencies to smart contracts. That’s the web3 security culture shift we’re building at Fidesium.
What do you think?
Would you have noticed the address change before approving the transaction?




